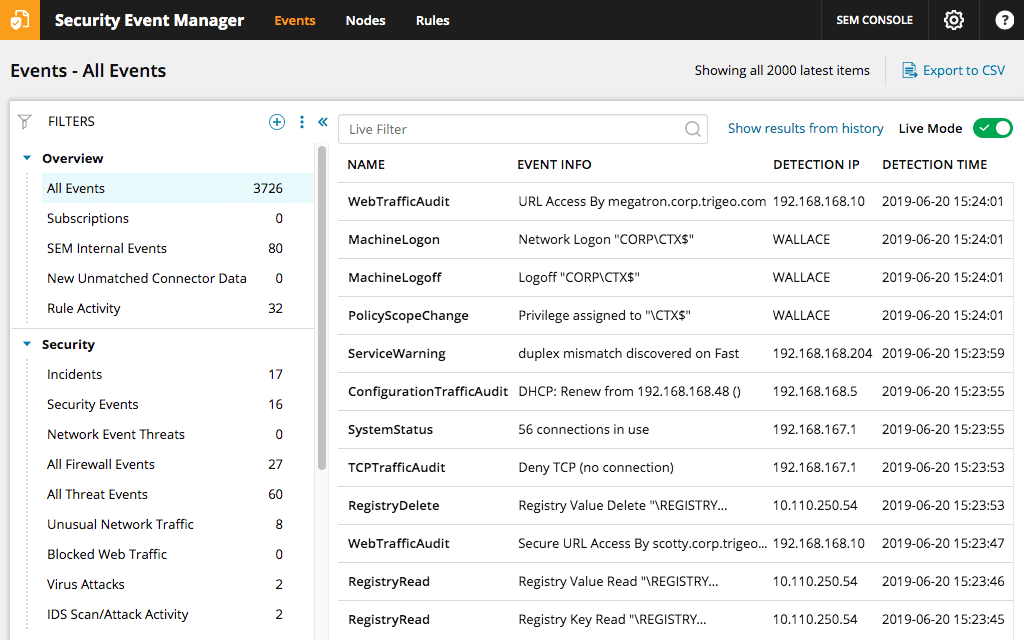
Threat detection for on-premises networks shouldn't be complicated.
Do you find yourself asking these questions?
What can I do to be aware of security threats?
SEM's cyberthreat intelligence framework can help you identify suspicious activities.
How can I make complex compliance reporting easier?
SEM provides hundreds of out-of-the-box reporting templates to help make demonstrating compliance easier.
How can I track file and directory access, movement, and shares?
Use SEM's file integrity checker to view details of changes made to files and folders.

Our SIEM tool is an industry favorite. Hands down.
“... unless they have a registered USB drive, I block it. LEM does all that for me.”
"Using SolarWinds LEM forensic capabilities, we were able to demonstrate to investigators and customers that a data breach had not occurred at our location where our clients’ data was stored. Being able to prove that no compromise had occurred saved us from a potentially large civil action lawsuit."
"We had accounts that were being locked. In the past we had to look at every log, every server. With LEM, it gave us one picture showing us everything."
"We are just finishing up with our PCI certification as a service provider, and the amount of work required is significant. Our auditors were also familiar with OSSEC; however, they were also familiar with LEM and several other tools. Because of our use of LEM, we breezed through the log management components of PCI."
“... by bringing [LEM] in, we can definitely get an in-depth view of what’s going on in our environment.”
"Certain employees attempted to pass off sensitive financial information via USB to a cell phone. The USB rule disconnected the device and fired an email to administrators."